A Nationwide company with offices in Miami : Fort Lauderdale
West Palm Beach: Naples: San Juan, Puerto Rico : Medellin, Colombia
Security Solutions
We’ve partnered with industry leaders to implement secure protection for everything from your data and brand to your property and network.
How Secure Are Your Systems?
Comprehensive security solutions are more than having a firewall in place and a locked front door. The heartbeat of your business is your customer data and financial exposure, and every day we see front page headlines for data breaches, even at Fortune 500 enterprises. Small businesses are attacked daily as well, and often the damages are so devastating that they never recover, both in terms of financial losses and reputation.
Cloud Integrated Technologies Inc. recognizes that security is also more than technology… it is about the technical solutions, processes to evaluate and react to potential threats, vulnerabilities, and impacts, plus user training and education.

Key Security Services
- Penetration Testing & Environment Audits
- Full Security Operations Center (SOC) as a Service
- Physical security protection (IP cameras / door entry / video)
- Web and Application Firewall Management
- DDoS Mitigation
- SIEM Platforms & Reporting & Monitoring
- Virus, Malware, Spyware, Email Scanning
- Compliancy Attestations
- IDS/IPS Management
- Endpoint & Device Security Management
- Virtual CISO
- Disaster Recovery and Backups
- Data Loss Prevention (DLP)
- East/West Traffic Monitoring & Breach Protection
- Behavioral Management / Staff Training & Awareness
- Professional Services Security Consulting

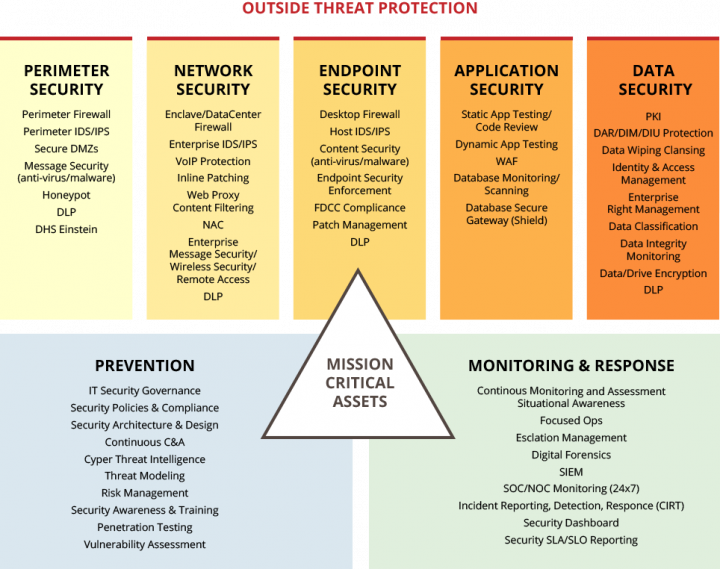
Layers of Security
Cyber security and physical security is not just about technology. While technology plays a substantial role, alone it is not enough to protect you from modern vector attacks. Cloud Integrated Technologies follows the ISO 27001 standard that recommends every comprehensive security solution address all areas of information security risk including people, process & technology. By following this standard, we are confident we can help protect your mission critical assets, and bring the solutions required to protect, monitor, and respond to attacks from all vectors – protecting more than just your data and your network, but also your brand and reputation.

Why Work With Us?
- Objective & vendor agnostic to evaluate multiple security options
- Will learn your business structure and goals
- Will understand your IT infrastructure and vulnerabilities
- Will determine the optimal comprehensive security solution
- Will manage the implementation and support of the selected solution
- After implementation support including customer service and escalations
- Be integrated as part of your organization’s ecosystem
Contact Us for a Customized Security Services Review
Are security services the right solution for your business? To help you find out, we are now offering a complimentary Security Review to baseline your need and provide an overview of the cost savings or the efficiency gains available to your company.
You can call us at (954) 358-3669, or email us at gm@citsolutions.us to start a discussion.
We will get back to you as soon as possible.
Please try again later.
A Nationwide company with offices in Miami : Fort Lauderdale: West Palm beach: Naples :
San Juan, Puerto Rico : Medellin, Colombia
Solutions
About Us
In these times businesses depends on their connectivity to communicate and connect with customers and team members.
CIT keeps you connected so you can focus on your core business and keep you generating revenue from your customers and productivity from your team members.
Contact Info
(954) 358-3669 / (866) 290-7676
Monday – Friday: 9:00am-5:00pm
Saturday – Sunday: Feel Free to
Call 866-290-7676